What is External Attack Surface Management (EASM)?
External attack surface management (EASM) is the continuous practice of discovering and assessing Internet-facing assets and looking for their vulnerabilities and anomalies. Mapping out your attack surface with External Attack Surface Management will help you understand where and to what degree your Internet-facing assets are exposed.
Industry experts have highlighted Attack surface expansion for years, from Gartner and Forrester to KuppingerCole. Detectify's CEO, Rickard Carlsson, framed it as follows in an interview with HelpNetSecurity. "There is virtually no difference between office work and remote work anymore. There is no inside and outside, just outside. What is to be secured now is a growing, dynamic, and sprawling mess of endpoints, cloud services, and third-party applications that form an external attack surface."
Gartner also recognised Detectify as a Sample Vendor in the External Attack Surface Management Category in their research.
Greater use of the public and hybrid cloud and highly connected supply chains are leaving organizations vulnerable to attackers. For those working on the frontline of cybersecurity, identifying and monitoring changes in your external attack surface is crucial to discern what actions to take to protect the attack surface.
Learn more in the e-book: External Attack Surface Management - What it is and what it isn't
Are Attack Surface Management and External Attack Surface Management the same thing?
Attack Surface Management (ASM) is an evolving product category, with various methods and attack surface assessment technologies used to approach the attack surface. Forrester defines Attack Surface Management as “The process of continuously discovering, identifying, inventorying, and assessing the exposures of an entity’s IT asset estate.” Attack surface management can be seen as a broader approach to detecting and handling vulnerabilities that weaken your security posture.
External Attack Surface Management is one of the Attack Surface Management processes whereby tooling “continuously scans for, discovers, and enumerates unknown internet-facing assets, establishes the unique fingerprints of discovered assets, and identifies various exposures.” External Attack Surface Management leverages an outside-in approach to understand what is being exposed on the attack surface.
What External Attack Surface Management isn't
To better understand EASM, we can have a quick look at what it isn't. EASM is not a standalone product or service. It's not a replacement for security testing, vulnerability management, or other parts of a security program. It's not for insider threats and it's not an asset inventory. We can also look at a couple of other concepts that differ from EASM.
Cyber Asset Attack Surface Management (CAASM):
Although CAASM solutions allow organizations to see all their assets, they don't generally apply vulnerability assessments to the assets discovered.
CAASM solutions offer an inside-out approach to covering the attack surface, which may work for some organizations. However, its reliance on API integrations makes it difficult to onboard and scale for organizations with a rapidly expanding attack surface.
Digital Risk Protection Services (DRPS):
DRPS solutions crawl the Internet to attribute assets to organizations and access parts of the Internet like the dark web. Like CAASM, DRPS solutions don't apply vulnerability testing to assets they discover because such assets, like social media profiles, cannot be tested.
DRPS solutions are likely useful for larger enterprise organizations that can implement findings produced into existing Threat Intelligence workflows. This makes DRPS solutions less valuable to organizations that need actionable information on assets that pose a risk to their business.
Read more: How does EASM differ from CAASM and DRPS?
What is the attack surface?
An attack surface refers to any interface, physical or digital, where an attacker could try to enter their own input or deploy an attack vector to get unauthorized access to a system and extract data or other sensitive information. It could also be used as a point within a chain of attacks.
While inventory and visibility are critical first steps in preventing attacks, they alone are not enough to protect the attack surface. Security teams around the globe are now looking for solutions that can help them better manage what they are exposing, as well as running low noise and high accuracy testing on newly discovered assets.
How to define the attack surface area
Organizations increasingly rely on SaaS services and products, meaning the digital attack surface is more than the firewall and network. It is now a sum of the available entry points of the different web applications publicly accessible on the Internet – both known and unknown assets.
Known assets
Known assets are the assets you know and monitor with extra care. These include the multiple subdomains under the domain, security checking apache installations, central web application, and login interfaces.
Unknown assets
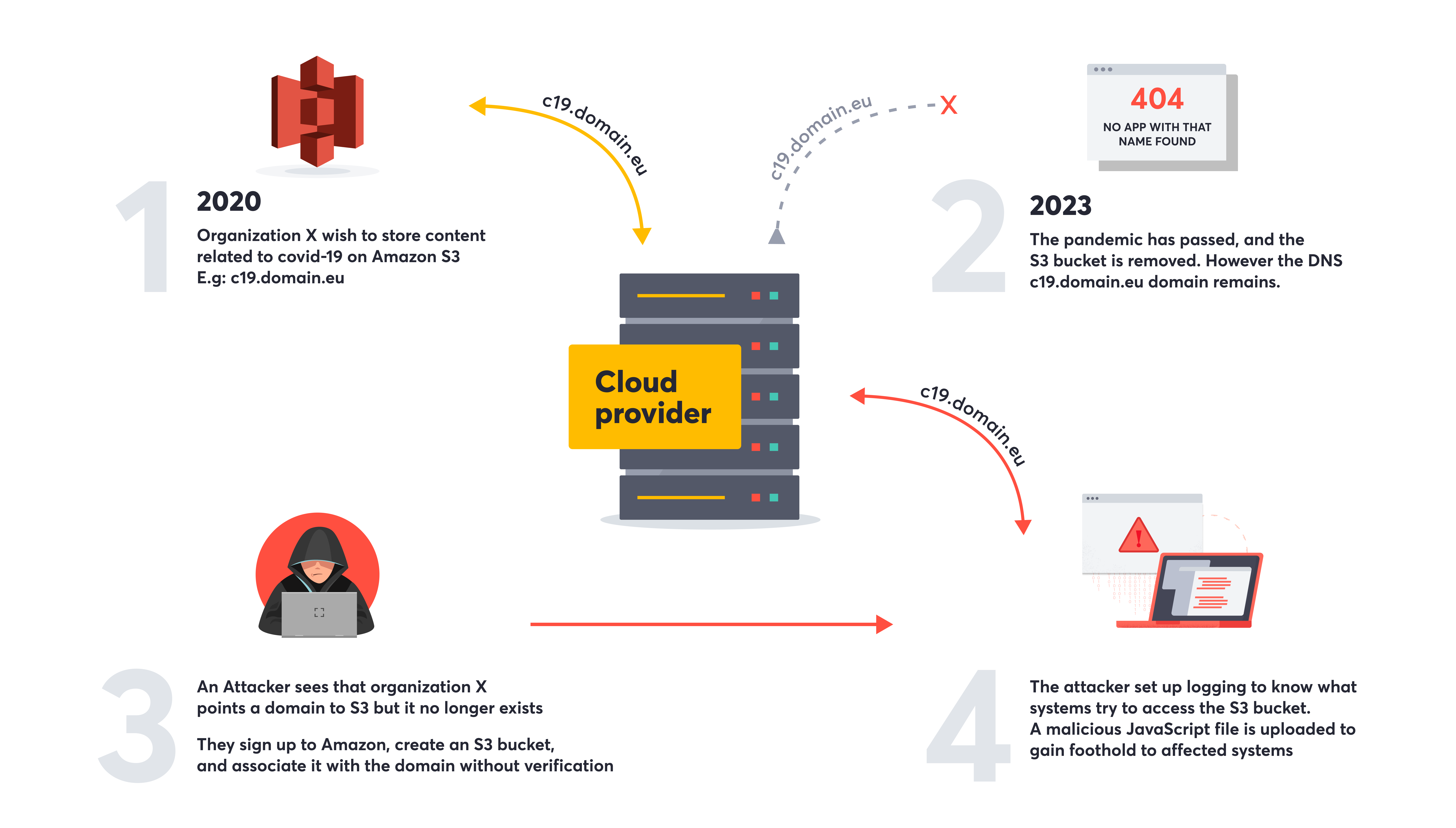
There will always be unknown assets that create weaknesses and blindspots in the attack surface. These can be harder to catch for a growing business without the right processes and tools and often occur when mistakes are made in the code, rogue or shadow IT software is installed, or the result of an insecure supply chain. There are also occasions when new vulnerabilities come up in existing code from a pentester or ethical hacker’s pure creativity of looking at where others aren’t.