
Catalin Curelaru
SECURITY TRIAGE LEAD, Visma"We have multiple public applications, and we want to be 100% sure that we are free from subdomain takeovers”Read more
Scale application security testing with confidence and efficiency
Discovery and vulnerability testing across the entire attack surface
Automatic scanning of web apps for business-critical vulnerabilities
Run in-depth scanning of your APIs
Scan internal applications and staging environments
Integrate Detectify with your security workflow
Eliminate the noise and manual work from traditional API scanning
Scan internal applications and staging environments
Integrate Detectify with your security workflow
9 out of 10 hackable apps are missed - cover what matters
Find dangling DNS to prevent hostile takeovers
ASM that scales alongside rapidly growing attack surfaces
Demonstrate real compliance every day
How Detectify customers benefit from our community of elite ethical hackers
Meet some of our ethical hackers who come from all corners of the globe
See which ethical hackers are leading for the quarter, year, and all time
Learn what Crowdsource is and how we're not your average bug bounty platform
How to join, submission types, 0-day rewards, and payment information
Technical and security research blog featuring write-ups and how to guides

Ready to join? Solve our Crowdsource Challenge and become part of our community
Explore case studies, webinars, e-books, whitepapers and videos
Learn how Detectify is an essential tool in these customer stories
Webinars and recordings to level up your AppSec knowledge
Browse and download e-books and whitepapers on AppSec and related topics
Register and browse for both online and in person events and webinars
Read the latest product updates, news, industry insights and best practices
Browse and download e-books and whitepapers on AppSec and related topics
Register and browse for both online and in person events and webinars
Read the latest product updates, news, industry insights and best practices
Our External Attack Surface Management platform scales alongside rapidly growing attack surfaces, whether you're a digital-first product organization, a distributed company with many subsidiaries, or focusing on digital transformation.

"We have multiple public applications, and we want to be 100% sure that we are free from subdomain takeovers”Read more
The exposure knowledge supplied by our platform is critical in helping organizations uncover what they don't know they're exposing to the Internet. Find unknown precious assets, protect yourself from subdomain takeover, and become aware of other vulnerabilities and anomalies that you didn't know existed.
Automatically scan custom-built apps and find business-critical security vulnerabilities before hackers do. Detect the latest vulnerabilities that other tools can't find, including vulnerabilities found today.
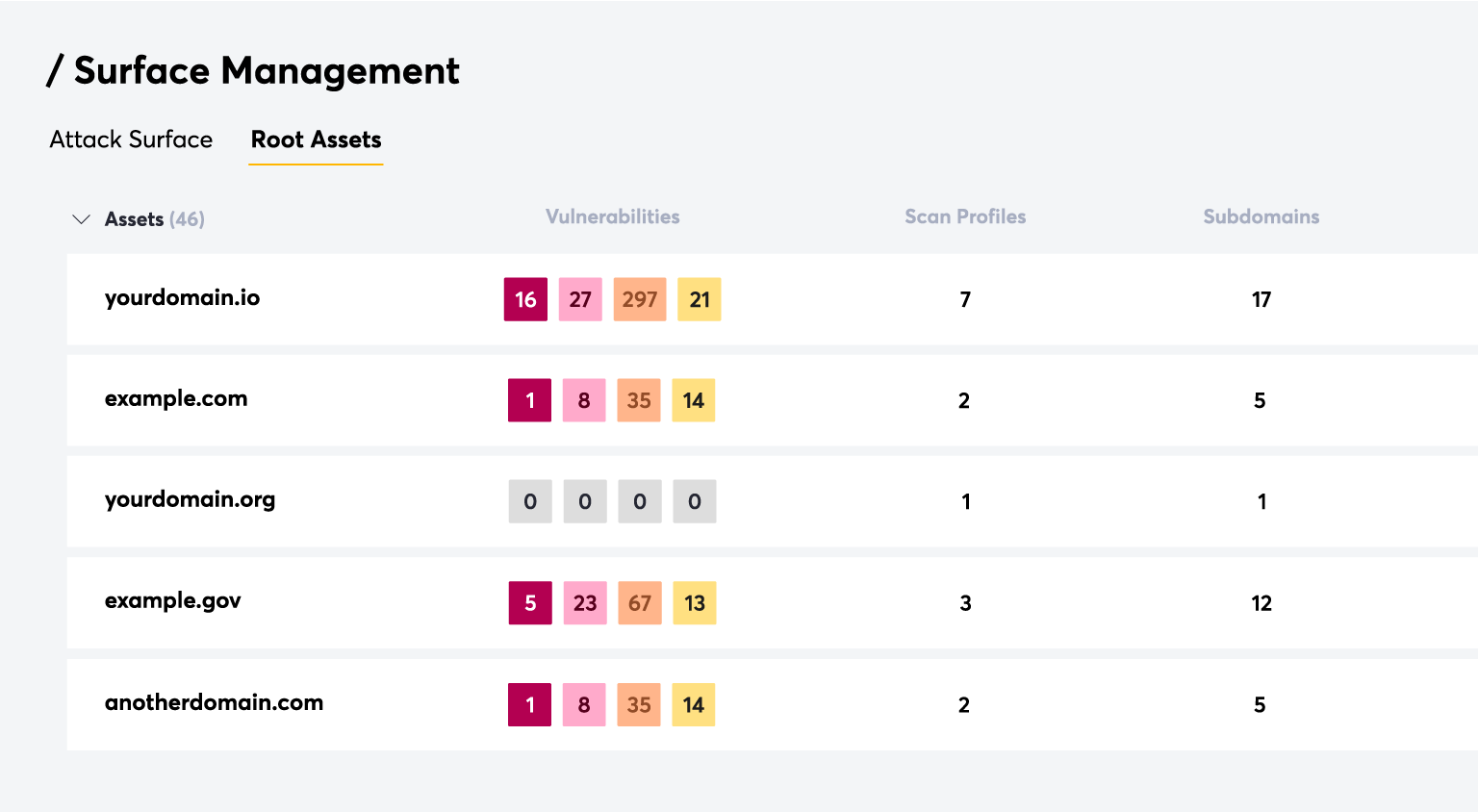
We provide actionable insights on assets and vulnerabilities that can be easily implemented into your existing workflows through various integrations or our powerful API.
Our automated and continuous monitoring enables developers to code more consistently and work directly with security teams to collaborate and prioritize vulnerability management.
Different ways to test for subdomain takeover
Accuracy rate
Payload-based testing
From subdomain takeovers to vulnerabilities in third-party services, chasing a dream of complete coverage makes it difficult to focus on what matters the most: getting accurate information about your attack surface as things change.
The only way to protect your attack surface is to hack it, and that's why we have built a solution that relies on ethical hackers around the globe who constantly discover new vulnerabilities in places you didn't even know were possible.
Read more about Crowdsource

Case study: BÜHLER GROUP

“Detectify has produced high-quality results with zero false positives, which is a significant advantage for Bühler.”

Patrick Zimmermann
INFORMATION SECURITY MANAGER
Discover known and unknown internet-facing assets and enable your development teams to ship code faster.
Every merger and acquisition increases your attack surface, making it more challenging to stay in control. Detectify's solution gives you more visibility and control over any inherited attack surface.
Discovers issues that are present in your supply chain and third-party apps.