
Michelle Tolmay
PHOTOBOX“With Surface Monitoring, we found subdomains we didn’t know we had”Read Photobox case study
Scale application security testing with confidence and efficiency
Discovery and vulnerability testing across the entire attack surface
Automatic scanning of web apps for business-critical vulnerabilities
Run in-depth scanning of your APIs
Scan internal applications and staging environments
Integrate Detectify with your security workflow
Eliminate the noise and manual work from traditional API scanning
Scan internal applications and staging environments
Integrate Detectify with your security workflow
9 out of 10 hackable apps are missed - cover what matters
Find dangling DNS to prevent hostile takeovers
ASM that scales alongside rapidly growing attack surfaces
Demonstrate real compliance every day
How Detectify customers benefit from our community of elite ethical hackers
Meet some of our ethical hackers who come from all corners of the globe
See which ethical hackers are leading for the quarter, year, and all time
Learn what Crowdsource is and how we're not your average bug bounty platform
How to join, submission types, 0-day rewards, and payment information
Technical and security research blog featuring write-ups and how to guides

Ready to join? Solve our Crowdsource Challenge and become part of our community
Explore case studies, webinars, e-books, whitepapers and videos
Learn how Detectify is an essential tool in these customer stories
Webinars and recordings to level up your AppSec knowledge
Browse and download e-books and whitepapers on AppSec and related topics
Register and browse for both online and in person events and webinars
Read the latest product updates, news, industry insights and best practices
Browse and download e-books and whitepapers on AppSec and related topics
Register and browse for both online and in person events and webinars
Read the latest product updates, news, industry insights and best practices

Detectify pioneered research into hostile subdomain takeovers. A decade later, we're still the number one tool to prevent DNS level vulnerabilities. With Detectify, you now have access to more than 600 unique tests for subdomain takeover vulnerabilities.
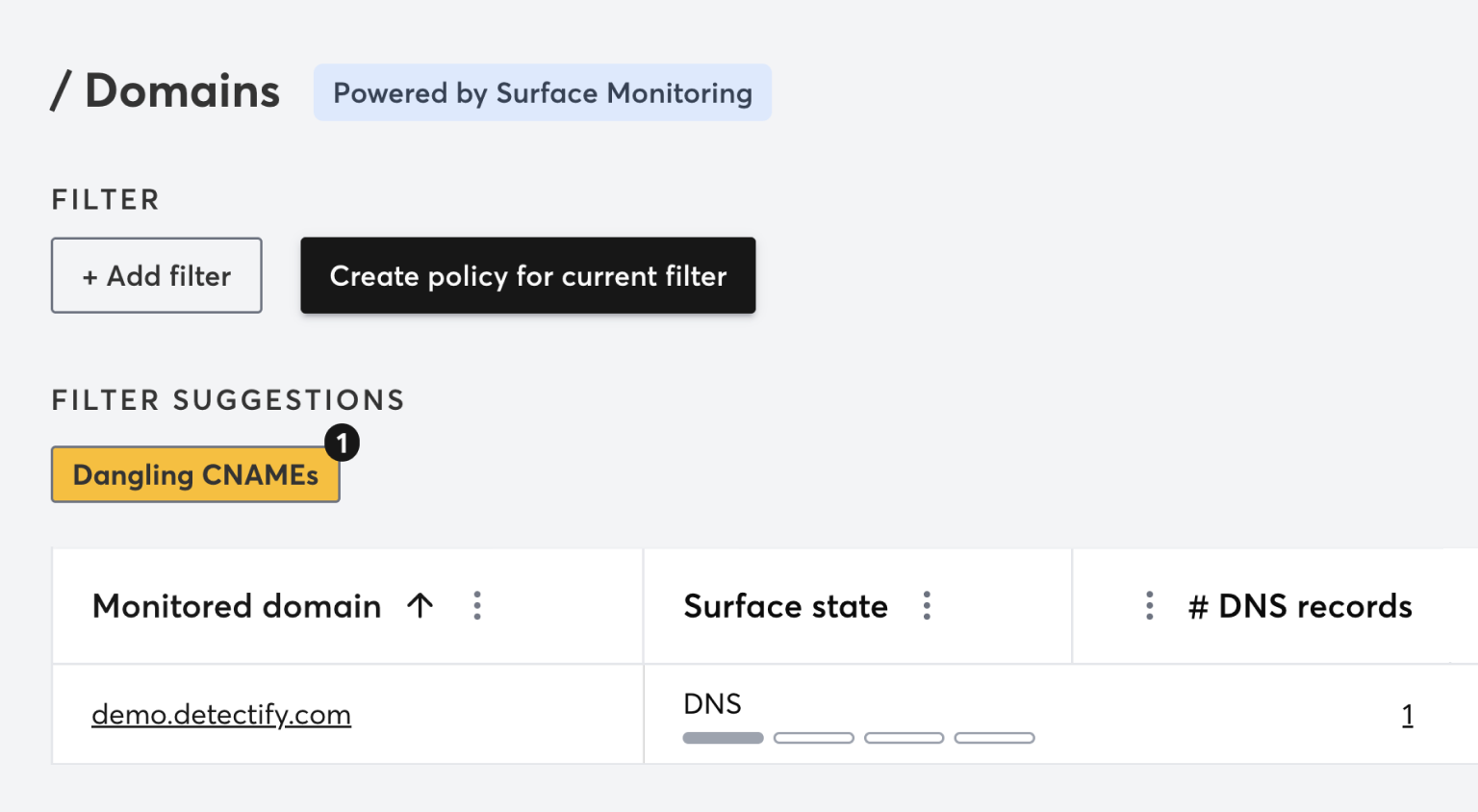
Detectify's Surface Monitoring is easy to set up. Connect to your DNS provider and start monitoring all your subdomains with a few clicks. Uncover unknown assets, cover DNS infrastructure and potential domain takeovers. Whenever a new subdomain is discoverable on the Internet, our tool alerts you and adds it to your inventory for continuous monitoring and vulnerability scanning.
Learn more about our platform
“With Surface Monitoring, we found subdomains we didn’t know we had”Read Photobox case study
Detectify were the first to research hostile subdomain takeovers as an attack vector back in 2014. From abandonware and mismatched DNS wildcards, we now run more than 600 tests for subdomain takeovers. It’s not uncommon to have hundreds of thousands of DNS records. While there are rigid processes for changes to firewall rules, changes to DNS records are usually made with much less oversight. For instance, development teams can update DNS records using Infrastructure as Code (IaC). With Detectify you can keep up with a sprawling DNS footprint and improve your security controls.
More on hostile subdomain takeover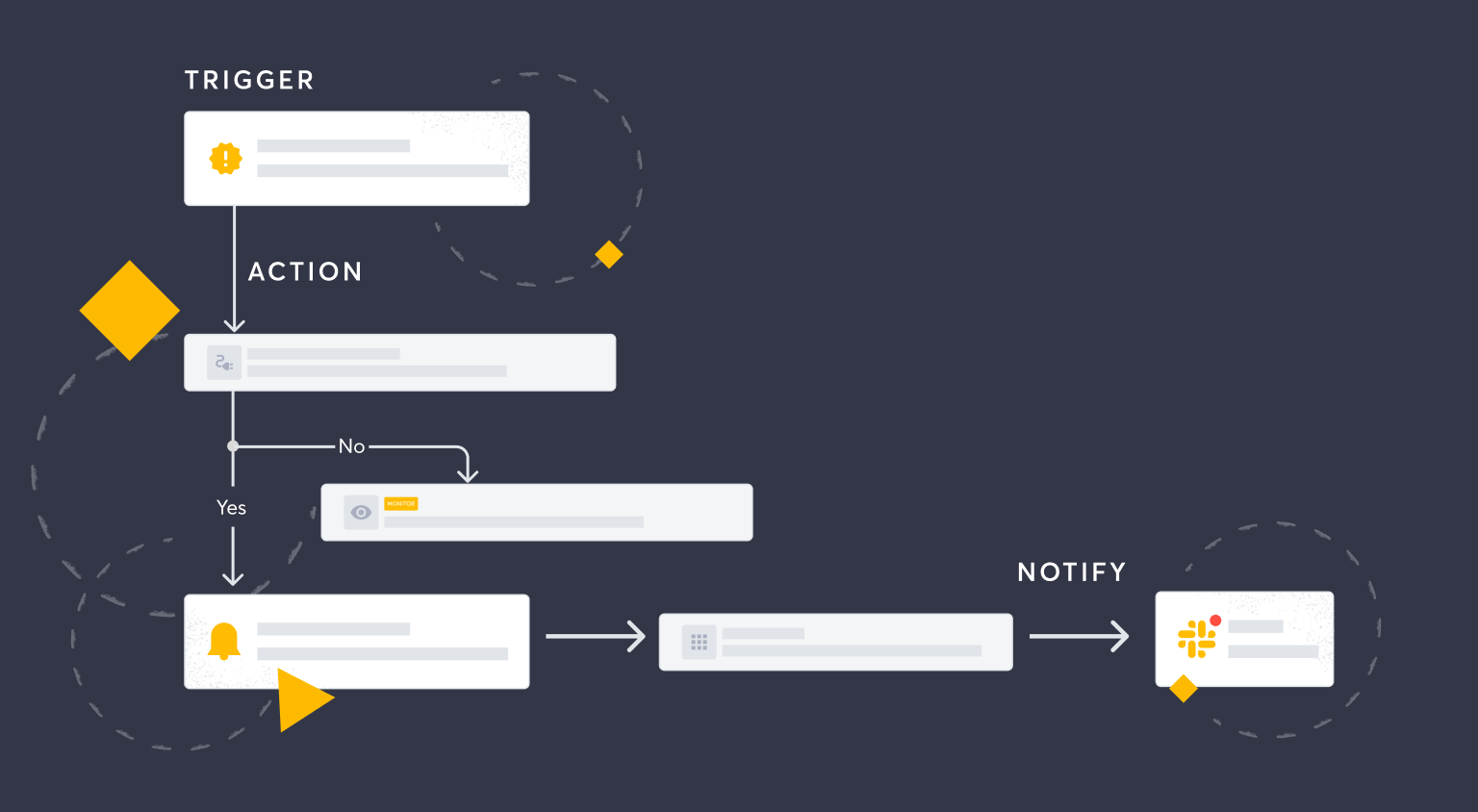
Detectify makes it easy to find dangling DNS records and potential subdomain takeovers. Findings without proper triage and remediation is yet of little value. Collaborate on the platform with members of your security team and developers. Or make use of our powerful integrations to fit your workflows. From Jira and Slack to Datadog and Splunk. Connect using Workato, a flexible iPaaS, or with our versatile API.
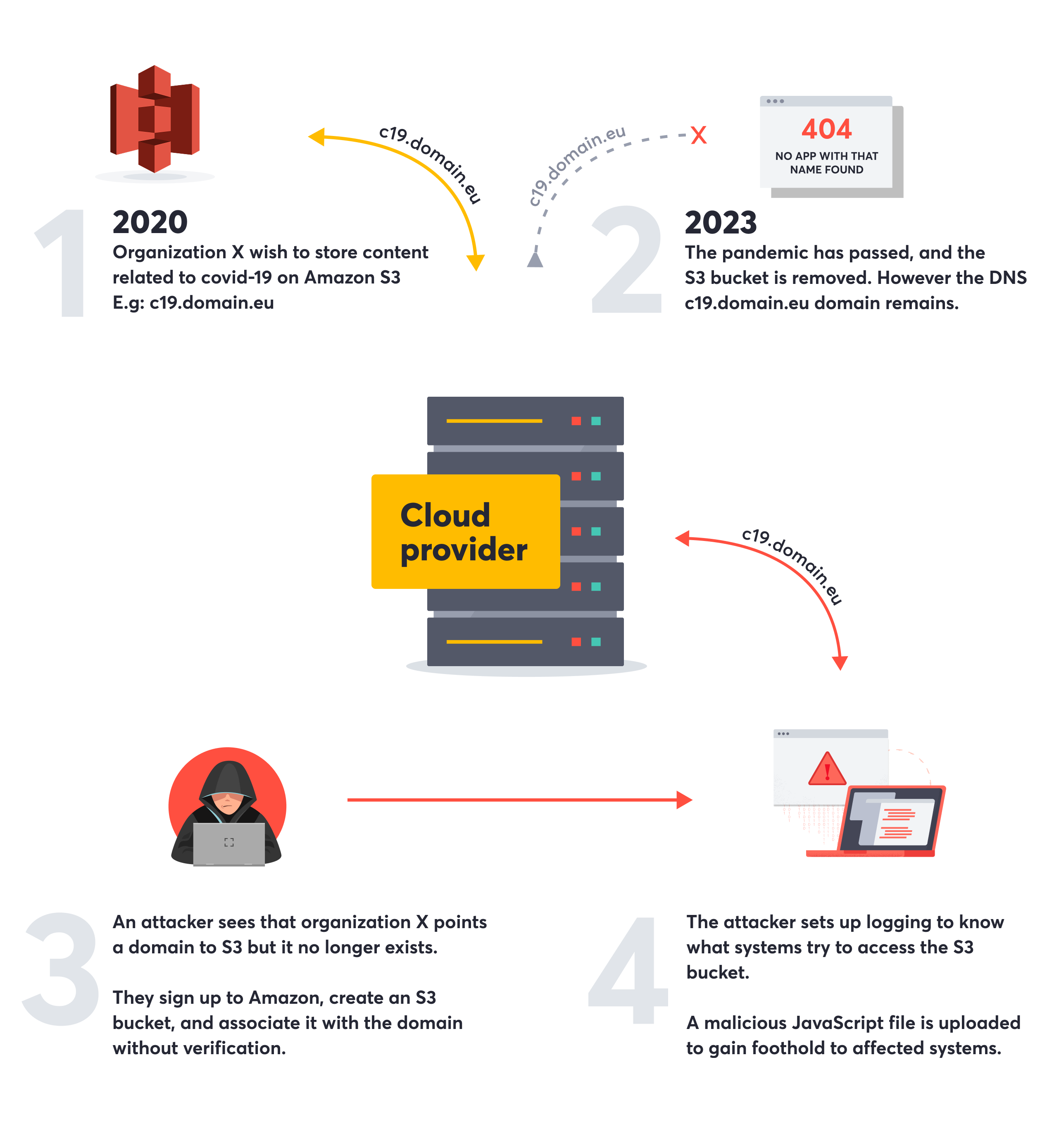
Subdomain takeover occurs when an attacker gains control of a subdomain belonging to a legitimate domain of the target. This often happens because the subdomain's DNS record hasn't been properly de-provisioned or points to a service that is no longer in use. Hostile subdomain takeover is a term coined by Detectify Security Researchers (read the original writeup). It refers to when an attacker takes control of a service no longer in use but that the target still has a DNS record pointing a subdomain to. As the DNS record points to a vacant service, this is also referred to as dangling DNS entries.
The severity of a subdomain takeover is very contextual. The takeover is usually only considered severe if it compromises other systems or gives direct access to user data (such as cookies).
Spinning up a fake page on the compromised subdomain for phishing purposes is bad enough. Consider an attacker getting control of one out of many Name Server (NS) delegations for the root (apex) zone. Then the severity can get worse than the most critical form of SQL injection. This can, over time, give the attacker access to all traffic destined for the vulnerable domain, including all its subdomains.
From subdomain takeovers to vulnerabilities in third-party services, chasing a dream of complete coverage makes it difficult to focus on what matters the most: getting accurate information about your attack surface as things change.
The only way to protect your attack surface is to hack it, and that's why we have built a solution that relies on ethical hackers around the globe who are constantly discovering new vulnerabilities in places you didn't even know were possible.
Learn more about Crowdsource


Case Study: Grammarly

“Surface Monitoring is an impressive product as it allows us to manage all of our subdomains and quickly search for new vulnerabilities.”

Vladimir Suslenko
Application Security Lead, Grammarly