Stop wasting time manually verifying security policies
Great security policies empower teams to work autonomously. However, validating that security policies are implemented is easier said than done. That's why Attack Surface Custom Policies help security teams set customizable policies on their external attack surface, leaving time to focus on the issues that matter most.
Book a demo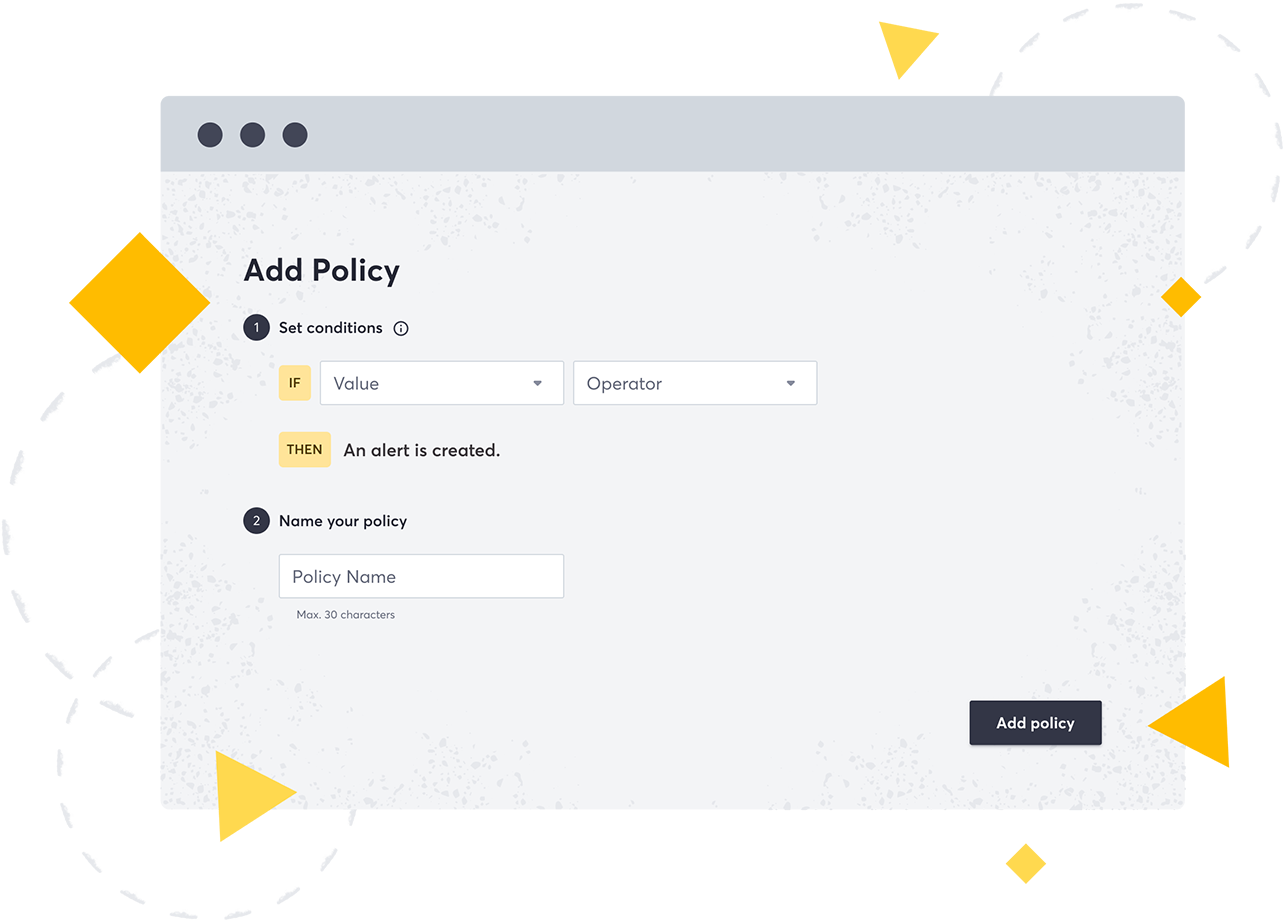
Security teams are enablers, not gatekeepers
Product and AppSec teams know how useful and clearly-defined security policies are simple to implement, scale, and verify. Implementing great security policies empowers teams to work effectively while maintaining autonomy. However, many Product and AppSec teams struggle to enforce their internal security policies, such as requiring security headers.
In an analysis of security headers by Detectify’s internal security team, the team found that in the sample of websites surveyed, not a single country had a website with all available security headers. This is no surprise, as there are no simple methods to verify that security headers are available to security teams.
What are Attack Surface Custom Policies?
Attack Surface Custom Policies are completely customizable rules that monitor for policy breaches as they occur in production. If a policy breach is detected, an alert is produced with helpful insights to help accelerate remediation.
Attack Surface Custom Policies leverage the complete coverage capabilities of Surface Monitoring to monitor your external attack surface continuously, ensuring your clearly-defined security policies are enforced, no matter the size of your attack surface.
Policies can be of any desired specificity and can be combinations of dimensions, such as open port data, web technologies, hosting providers, domain names, or DNS record types, to list a few examples. Today, the feature is available for custom policies when filtering open ports, specific technologies, geographies, and DNS settings.
How do Attack Surface Custom Policies work?
- Policies are set on your external attack surface using IF-THEN logic.
- As soon as a policy is set, we will begin monitoring it.
- If a policy is broken, an alert in the tool is created.
- Attack Surface Custom Policies are currently available to Surface Monitoring customers.
The unique benefit for users of Surface Monitoring is the customization of custom policies, something that is not currently available on the market. Unlike pre-set conditions that users can toggle on/off, Attack Surface Custom Policies offer real flexibility built on rules users can define based on their business context.
What problems do Attack Surface Custom Policies solve?
Great security policies empower teams to work autonomously, moving work forward as it should. However, validating that your security policies are actually implemented is difficult. Attack Surface Custom Policies will allow security teams to work proactively to reduce various risks that they previously would not have been able to identify.
Examples of Attack Surface Custom Policies you can set up today:
I want to know if there are any open ports except ports 80 and 443. Catch unexpected open ports that may not be on your allow list.
I want to ensure that there are no open ports on various protocols, like FTP, SSH, etc. Spot open ports such as ports 20, 21, 23, etc.
I want to know if we are running any instances of WordPress. Create an alert if WordPress is fingerprinted on my attack surface.
I want to know if my DNS configuration has any dangling CNAME records. Create an alert to spot dangling DNS issues and prevent subdomain takeovers.
Visit our Knowledge Base to learn how to start setting up custom policies.

