A platform for advanced application security testing
Detectify lets AppSec teams scale application security testing with confidence and efficiency. Cover 100% of your attack surface by pointing scans to endpoints that matter. Run more lightweight testing of the rest of your attack surface.
A complete solution for modern AppSec challenges
AppSec requires a new approach. Detectify provides a complete, integrated platform that moves with you through the entire security lifecycle: From discovery and prevention to deep testing and streamlined remediation.
First, gain complete visibility and control
You can't secure what you don't know. Our platform starts by mapping your entire external attack surface, from shadow IT and forgotten subdomains to unknown APIs.
- Discover your entire external attack surface automatically.
- Eliminate shadow IT and asset sprawl.
- Find and inventory all your unknown and undocumented APIs.
- Map assets acquired through M&A in minutes, not months.

Proactively prevent breaches at scale
Once your surface is mapped, we continuously scan for thousands of common, high-impact vulnerabilities—like subdomain takeovers and exposed technologies—that attackers exploit every day.
- Continuously monitor for critical DNS misconfigurations and takeovers.
- Identify exposed services, open ports, and outdated technologies.
- Enforce technology governance by finding non-compliant libraries.

Focus your resources on what matters most
Don't 'boil the ocean'. Our platform helps you identify your critical applications and APIs, so you can run in-depth, authenticated tests for complex OWASP Top 10 vulnerabilities.
- Run deep, payload-based tests on your most critical web apps.
- Test authenticated areas behind your login pages with ease.
- Find complex API-specific flaws like BOLA and Prompt Injection.
Deliver results, not noise
Security data is useless if it isn't actionable. We deliver high-signal, verified findings directly into your team's workflows and provide C-level dashboards to prove your posture.
- Onboard your entire attack surface in minutes, not weeks.
- Integrate high-confidence findings directly into Jira, Slack, and other tools.
- Demonstrate continuous security posture to leadership and auditors.

How does Detectify work? Watch a short demo
AppSec teams use Detectify to expose how attackers will exploit their Internet-facing applications. See how you can do the same.
Discover our platform's products
One platform for comprehensive coverage of your attack surface
API Scanning
Dynamic, accurate, and ongoing assessment of APIs that deliver high-accuracy, actionable findings.
API scanning that is dynamic on a new level
Proprietary, research-led testing
Unified API visibility
Application Scanning
Find and remediate business-critical vulnerabilities in custom-built apps with advanced crawling and fuzzing.
Render and crawl a custom-built application for in-depth findings
Maintain state and test authenticated areas
Scan massive applications with smart page filters
Dynamic scanning at scale
Surface Monitoring
Get a comprehensive view of your attack surface and secure your domains, apps, and APIs. Classify discovered assets and get recommendation where to dig deeper using Application and API scanning.
Detectify features
Discover some of the platform's features
Attack Surface Custom Policies
Proactively reduce risk by setting, enforcing, and scaling customizable security policies across your attack surface.
- Validate that your security policies are implemented
- Ensure security headers are enforced
- Spot technologies that aren’t approved for use
- Catch unintended open ports across your attack surface
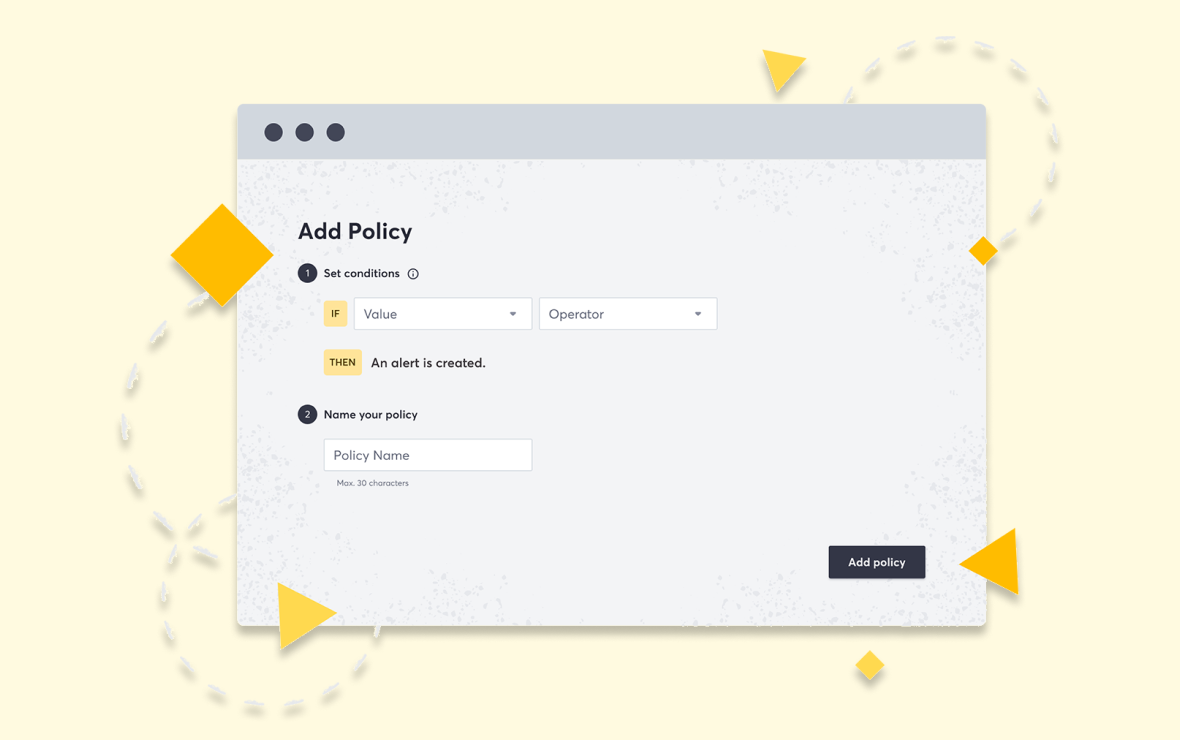
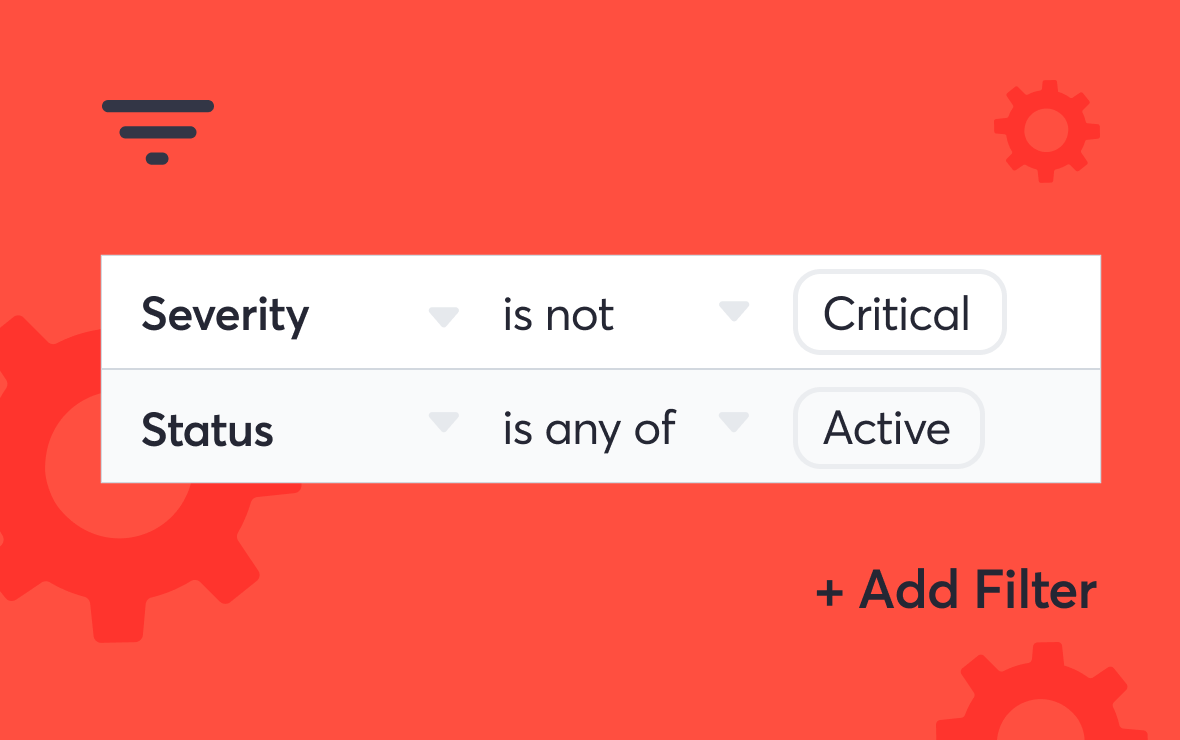
Vulnerabilities page
View, sort, filter, and export findings
Get an overview of the current state of the vulnerabilities on your attack surface.
- Combine multiple filters to narrow down vulnerability information
- Address threats on your web applications that matter the most
- Export findings when needed
- Suppress findings that aren’t an issue and mark them as an acceptable risk
- Filter for specific vulnerability types or severity scores
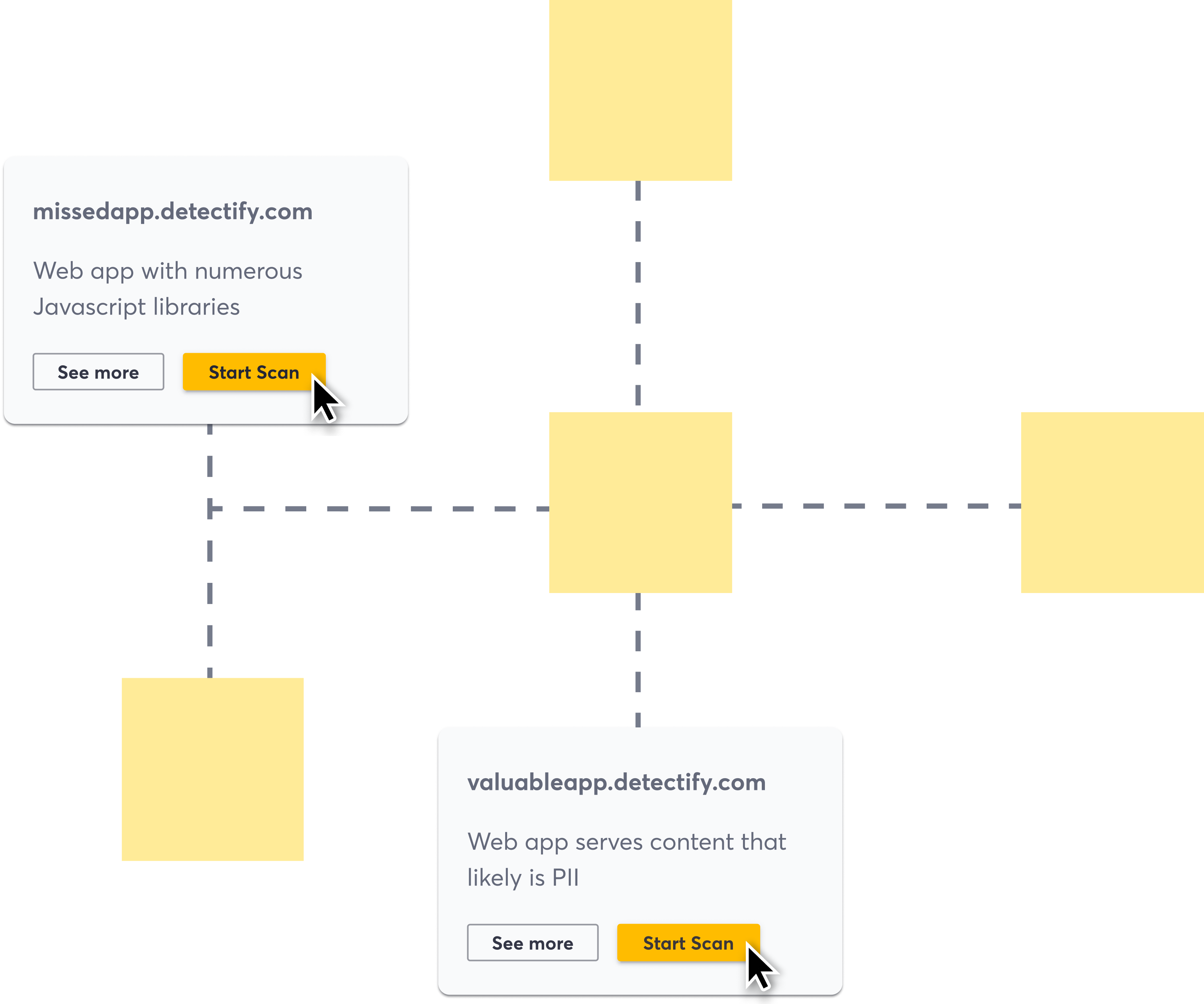
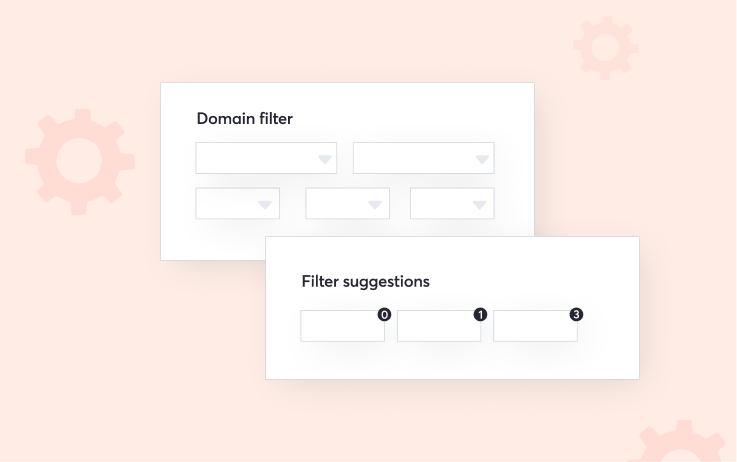
Domains page
Powerful and flexible attack surface insights
- Filter data across all of your domains by adding your own values or using suggested filters
- Create attack surface custom policies based on set filters to be alerted of breaches
- Visually explore dependencies across your domain data using the network graph
Attack Surface View
Get a complete overview of your assets
- Access all your assets, technologies, and root assets on one page
- Five different levels of ‘Surface State’ indicate to what level an asset is exposed on your attack surface

Integrations / API
Customizable integrations and effective triaging of vulnerability findings
- Centralize vulnerability findings in one place, such as through a Vulnerability Management (VM) platform
- Pre-set integrations with popular tools, including Slack, Jira, Trello, Microsoft Teams, Splunk, OpsGenie, and HTTP webhooks
- Customize how you work with vulnerability data, reducing noise and remediating faster