1,700+ global customers choose Detectify to cover their attack surface
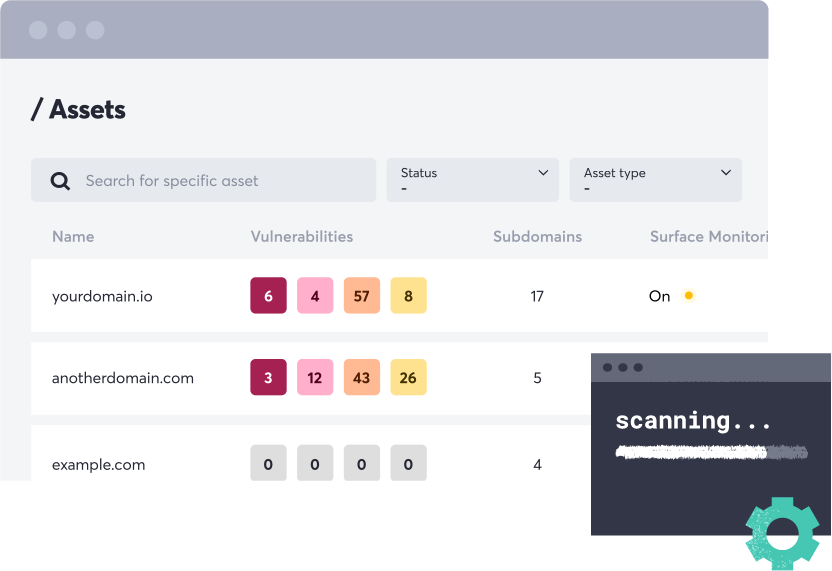
Automated scanning fueled by research from elite ethical hackers
We have always sought to automate human ingenuity. From pioneering subdomain takeover tests to crowdsourcing vulnerability research, including hundreds of 0-days. We build our own engines so that we can move at speed and scale. When new vulnerabilities like Log4Shell and CUPS pop up, we have tests out in hours not days.
Vulnerability testing on all your external assets
Detectify goes beyond signature-based vulnerability testing and identifying what's on the attack surface. We scan every exposed asset with dynamic application testing methodologies. Tracking attack surface changes such as your DNS footprint including ports and technologies. This is guiding our deeper tests and gives you a better sense of where to focus your efforts and resources.
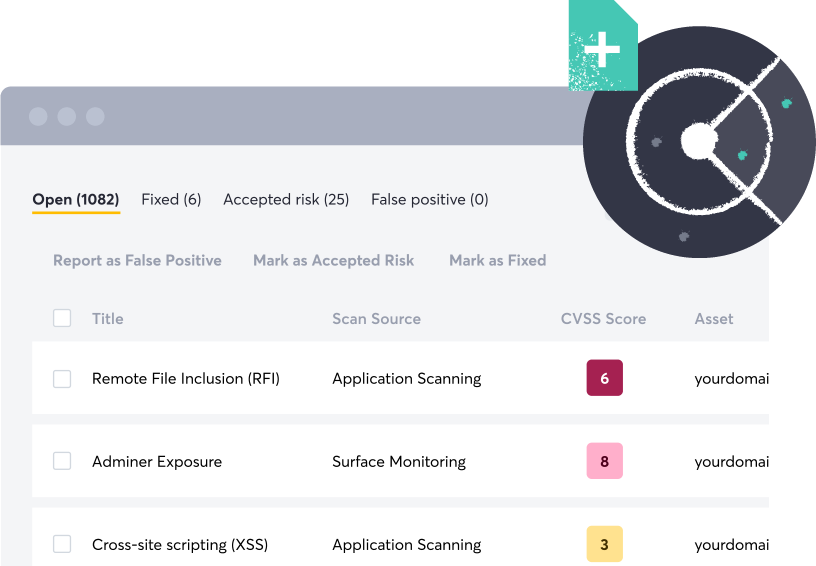
Not all findings are created equal, focus on what’s actually exploitable
Before we even begin testing a single asset, we have already taken several steps to ensure the results are relevant and accurate. We don’t build every CVE test available like many open-source tools. Because we fingerprint our customers' entire attack surface daily, we know what technologies they are using. Based on this data, we only build tests into our engines that are relevant to our customers’ tech stack. Going one step further we only build automated payload-based tests so for every new finding, you can trust that it is a vulnerability an attacker can find and exploit.
Get value as soon as you turn on the tool
Detectify doesn’t require hours of work to onboard and manage. Get started in no-time using cloud connectors and easily integrate results into your existing workflows. Get the most out of the platform with powerful integrations and API.
GO HACK YOURSELF
Check your web apps for vulnerabilities today
Join 1000s of companies that continuously scan, detect, and remediate business-critical vulnerabilities with our vulnerability scanner.
What is Vulnerability Scanning

Vulnerability management
Vulnerability scanning is key to effective vulnerability management. Scanning identifies potential weaknesses in systems and applications. Vulnerability management covers the broader process of addressing them. Scanning data allows for prioritization and remediation of vulnerabilities based on risk. This systematic approach minimizes your attack surface and reduces the risk of exploitation. In essence, scanning provides the crucial data that drives the vulnerability management process.
Application security testing
Application Security Testing (AST) is crucial for robust vulnerability management. Within that category, Dynamic Application Security Testing (DAST) can prove especially valuable. DAST focuses on live applications, simulating attacks to find weaknesses like SQL injection. This real-world testing provides more accurate results than only analyzing code. You cannot even catch certain vulnerabilities in development. Adding exploitability to result, prioritization of which to fix first becomes easier.

Attack surface management
Attack Surface Management (ASM) boosts vulnerability management by mapping your entire digital footprint. As with DAST, taking an external approach can give you the hacker perspective. External Attack Surface Management (EASM) is one of these outside-in views. While regular scanning focuses on known assets, EASM discovers all internet-facing assets. Unknowns can include forgotten apps, cloud resources, or DNS records. The latter leaves you vulnerable to subdomain-takeover attacks. Adding attack surface finding helps you assess and fix all exposed assets. This minimizes blind spots and reduces the risk of attackers exploiting overlooked weaknesses.
Vulnerability testing the Detectify way
Effective vulnerability management requires a comprehensive understanding of your attack surface. Mapping all your internet-facing assets uncovers what you need to look closer at. Revealing old apps, exposed databases, and assets you might not even know you had. These overlooked systems can be easy targets. Digging into critical areas by simulating real-world attacks will uncover exploitable vulnerabilities. Reducing the risk of exploitation, you want to identify, assess, and remediate all potential entry-points. With both broad and deep testing, your vulnerability management gains a comprehensive picture.
Included in a 2-week free trial:
No card needed to get started.
Surface Monitoring
2 apex domains with continuous monitoring for the whole trial period for broad attack surface coverage and testing.
Application Scanning
5 scan profiles (domains or subdomains), with unlimited scans per scan profile for deep application testing where it matters most.
Continuous coverage 24/7
Discover and monitor your modern tech stack with daily insights about every exposed asset.
Unique crawling and fuzzing engine
That goes beyond the capabilities of a “traditional” DAST scanner.
Accurate results that save time
99.7% accuracy in vulnerability assessments with 100% payload-based testing.
Ethical hacker expertise in 15 minutes
Research from Crowdsource, our community of 400+ ethical hackers, allows you to discover the latest undocumented security vulnerabilities.

Ted M
President
Small Business

“Detectify is a powerful tool that every business should have”
Detectify provides my customers with a point-in-time score about their current security vulnerabilities, their risk and a score. It has an easy to use interface, reporting that is interpretable by both the technical and non-technical alike, and best of all - it's affordable for what you get!
GO HACK YOURSELF
Start vulnerability scanning today
Find vulnerabilities and misconfigurations across your web apps and keep track of all Internet-facing assets and technologies.













