OWASP Top 10 web application security risks
OWASP is a non-profit organization aiming to improve software security. Their Top 10 is a critical resource, highlighting the most prevalent threats that expose your applications to attack. From data breaches to unauthorized access, these vulnerabilities can have devastating consequences. Understanding these risks is the first step in building a robust security posture. The OWASP Top Ten was first published in 2003 and is regularly updated to reflect the evolving threat landscape. These updates show the dynamic nature of application security and the need for continuous vigilance.
Broken Access Control
Access control failures typically lead to unauthorized information disclosure, modification, or destruction of data or performing a business function outside the user's limits.
Cryptographic Failures
Previously known as Sensitive Data Exposure, this category focuses on failures related to cryptography (or lack thereof), which often lead to exposure of sensitive data.
Injection
Some of the more common injections are SQL, NoSQL, OS command, Object Relational Mapping (ORM), LDAP, and Expression Language (EL) or Object Graph Navigation Library (OGNL) injection. Cross-site scripting (XSS) is now part of this category.
Insecure Design
A new category for 2021 that focuses on risks related to design and architectural flaws, with a call for more use of threat modeling, secure design patterns, and reference architectures.
Security Misconfiguration
A component susceptible to attack due to an insecure configuration would be classified as security misconfiguration.
Vulnerable and Outdated Components
A component with a known vulnerability could be an operating system, a CMS, a web server, an installed plugin, or even a library used by a plugin.
Identification and Authentication Failures
Previously known as Broken Authentication, this involves all kinds of flaws caused by errors in the implementation of authentication and/or session management.
Software and Data Integrity Failures
A new category for 2021 that focuses on making assumptions related to software updates, critical data, and CI/CD pipelines without verifying integrity.
Security Logging and Monitoring Failures
This category is to help detect, escalate, and respond to active breaches. Without logging and monitoring, breaches cannot be detected.
Server-Side Request Forgery
SSRF flaws occur when a web application fetches a remote resource without validating the user-supplied URL.
GO HACK YOURSELF
Test for OWASP Top 10 and beyond
Join 1000s of companies that continuously scan, detect, and remediate OWASP and other business-critical vulnerabilities with Detectify.
Common and severe threats Detectify test for
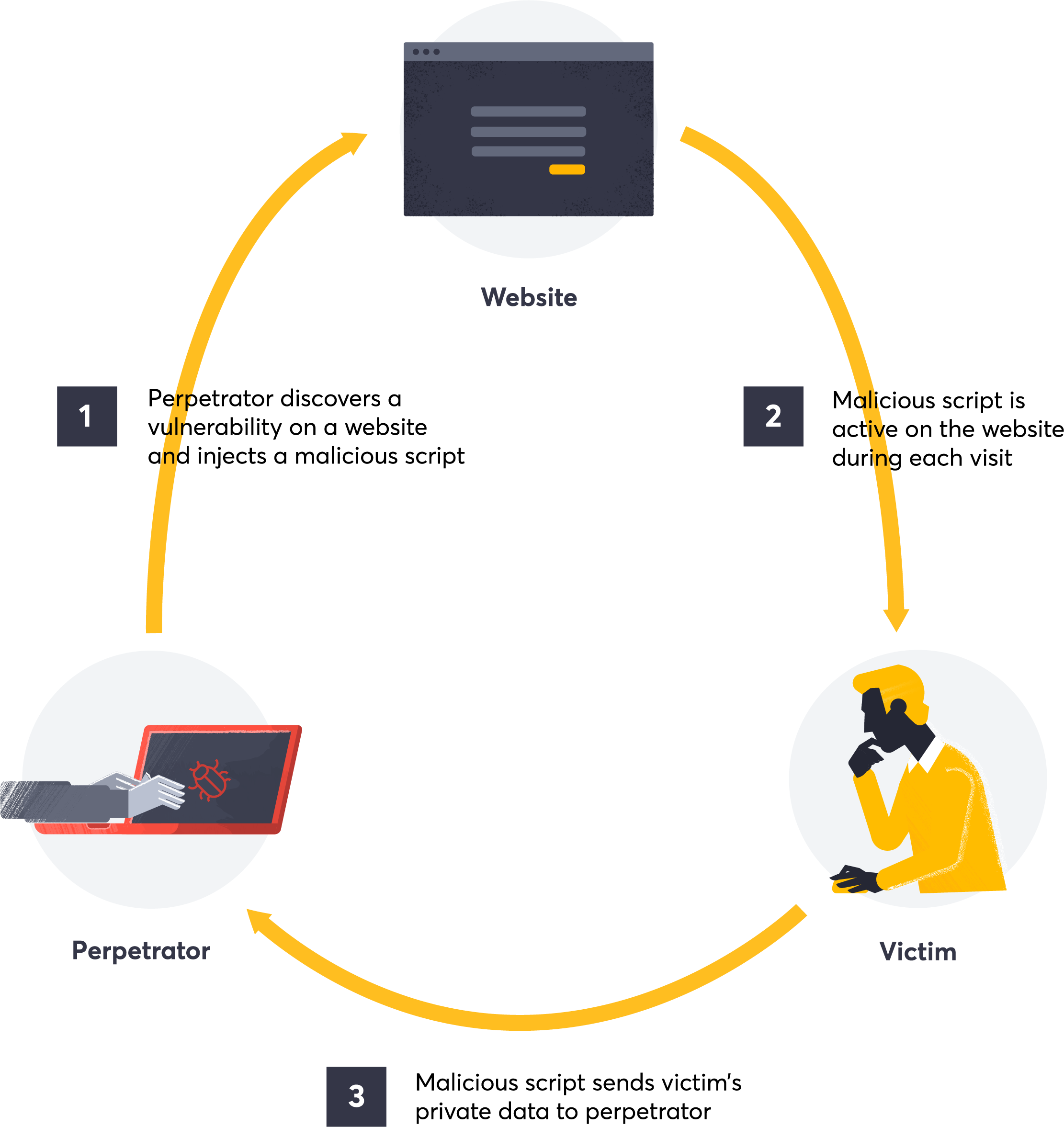
Cross-site scripting (XSS)
SQL injection (SQLi) vulnerabilities are by their nature very critical. A remote attacker will gain access to the underlying database. This is usually done in a similar fashion as with XSS, by inserting malicious code into input fields. However, the target and impact are fundamentally different. The malicious code injected in SQL injection attacks aim to manipulate the database. With the goal to alter or extract data, this impacts the database's integrity and confidentiality. In the worst case scenario it allows an attacker to read, write, and delete data, or even take control of the entire database server.
Without a good way of detecting an XSS attack, a user might be executing malicious code and handing over their data to an attacker. Attackers use XSS to steal cookies, hijack sessions, redirect you to malicious sites, or deface websites. The impact of XSS can range from subtle annoyances to catastrophic data theft. The latter leading to significant financial risk and reputational damage. Detecting and preventing XSS requires rigorous input validation, output encoding, and the implementation of Content Security Policy (CSP) to restrict the execution of untrusted scripts.

SQL injection attack
SQL injection (SQLi) vulnerabilities are by their nature very critical. A remote attacker will gain access to the underlying database. This is usually done in a similar fashion as with XSS, by inserting malicious code into input fields. However, the target and impact are fundamentally different. The malicious code injected in SQL injection attacks aim to manipulate the database. With the goal to alter or extract data, this impacts the database's integrity and confidentiality. In the worst case scenario it allows an attacker to read, write, and delete data, or even take control of the entire database server.
The prevalence of SQL injection stems from its simplicity and the widespread use of databases in web applications. Mitigating this risk is a lot about separating user input from SQL code, e.g. with robust input validation and escaping techniques.
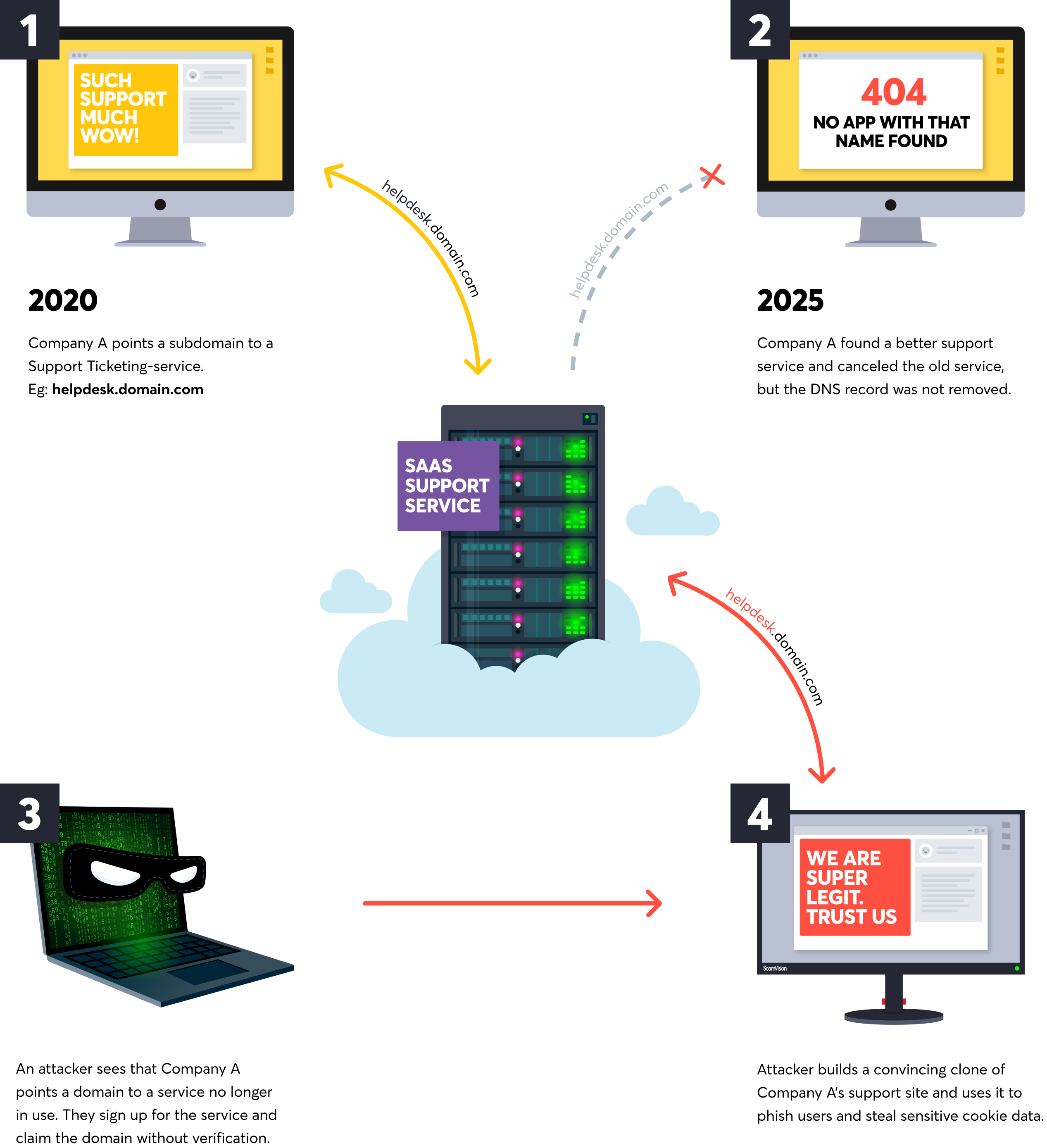
Subdomain takeover
Subdomain Takeovers is a critical but often overlooked type of vulnerability that is difficult to detect. Arising from misconfigurations across various aspects of web infrastructure, they are often classified under 'Security Misconfigurations'. Yet, its impact can manifest as elements of 'Broken Access Control' or even 'Injection' if the takeover leads to malicious injection. The vulnerability occurs when a subdomain's DNS records point to a service that is no longer in use, allowing an attacker to claim that subdomain. Or rather, claim the resources the DNS record points to. Examples can be cloud services like S3 buckets and Heroku, or SaaS like Shopify and Zendesk. This enables attackers to host malicious content under the guise of your legitimate domain. Letting them conduct phishing attacks or intercept sensitive data.
Detectify researchers pioneered subdomain takeover testing back in 2014. Since then, we've added over 600 types of tests for subdomain takeover vulnerabilities. More than any other tool available. The term Subdomain Takeover is the most common and widely understood way to describe this type of threat as it emphasizes the outcome. Another term used is Dangling DNS that focuses on the technical cause of the vulnerability. It describes a DNS record (specifically a CNAME record) that points to a service that no longer exists or is no longer controlled by the domain owner. More technically accurate, it highlights the orphaned or "dangling" nature of the DNS record.
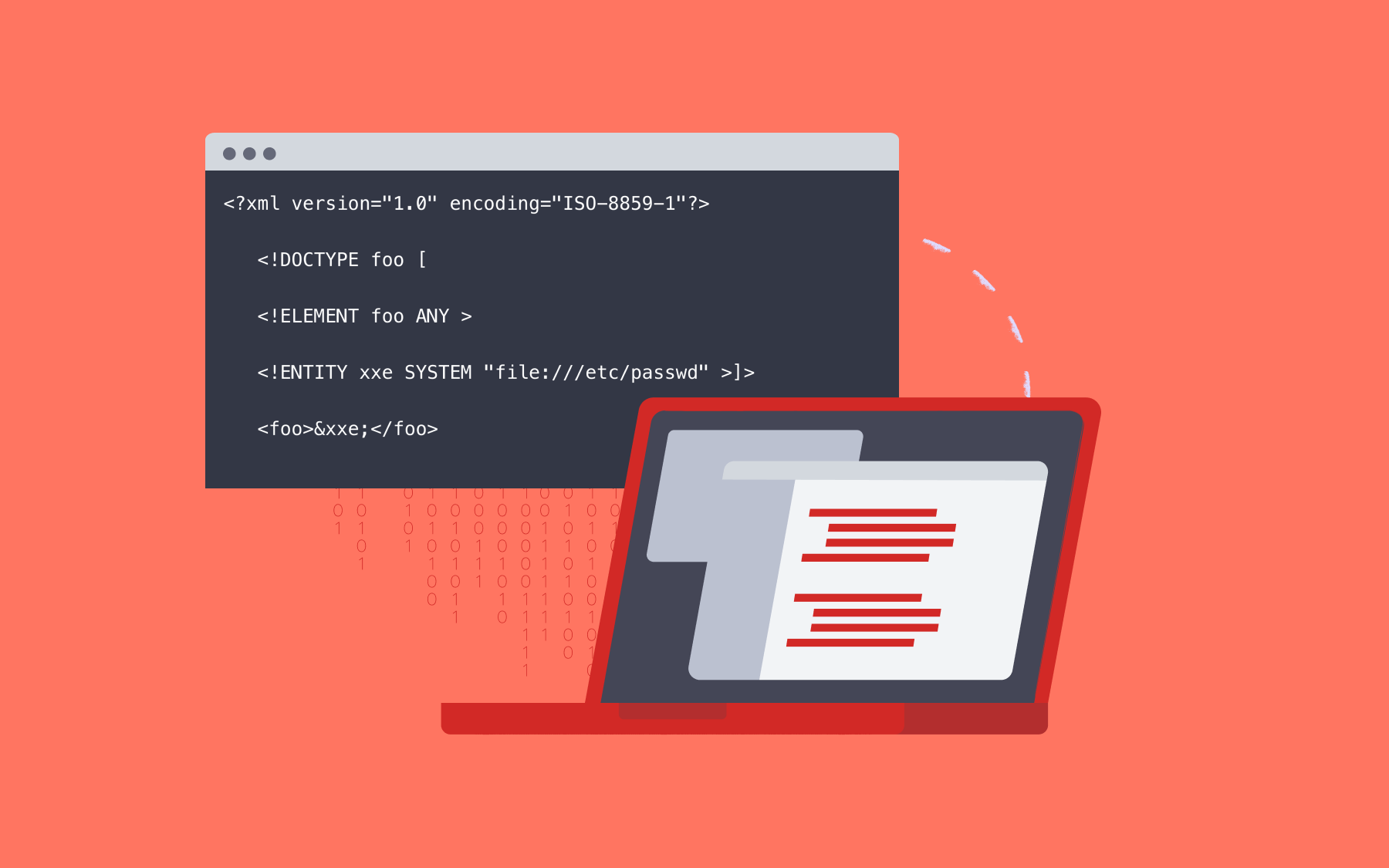
XML Injection (XXE)
Another common attack is XML External Entity (XXE) injection. Although it has 'injection' in its name, it sorts under 'Security Misconfigurations'. This makes sense if you consider OWASP's ambition to guide toward effective prevention strategies. In the case of XXE, the primary defense is to disable external entity processing in XML parsers, which is a configuration change.
XXE occurs when an application parses XML input that references external entities. Attackers can exploit this vulnerability to read files from the server, perform server-side request forgery (SSRF), or even execute arbitrary code.

Server-Side Request Forgery (SSRF)
In essence, Server-Side Request Forgery (SSRF) attacks aim to compromise a server. SSRF vulnerabilities allow an attacker to manipulate a server into making requests to unintended internal or external resources. Attackers use weak validation of user-supplied URLs or other input used in server-side requests. By exploiting SSRF, attackers can access internal services, databases, or even cloud metadata. Leading to data breaches, unauthorized access, and the ability to pivot within an organization's internal network.
While using injection as a method, SSRF can also be a form of 'Broken Access Control' as it bypasses intended network boundaries. Yet, Server-Side Request Forgery makes up its own category in the OWASP Top 10. The basis for this relies on input from the AppSec community on its importance, rather than its incident rate ahead of the 2021 list update.
Included in a 2-week free trial:
No card needed to get started.
Surface Monitoring
2 apex domains with continuous monitoring for the whole trial period for broad attack surface coverage and testing.
Application Scanning
5 scan profiles (domains or subdomains), with unlimited scans per scan profile for deep application testing where it matters most.
Continuous coverage 24/7
Discover and monitor your modern tech stack with daily insights about every exposed asset.
Unique crawling and fuzzing engine
That goes beyond the capabilities of a “traditional” DAST scanner.
Accurate results that save time
99.7% accuracy in vulnerability assessments with 100% payload-based testing.
Ethical hacker expertise in 15 minutes
Research from Crowdsource, our community of 400+ ethical hackers, allows you to discover the latest undocumented security vulnerabilities.

Ted M
President
Small Business

“Detectify is a powerful tool that every business should have”
Detectify provides my customers with a point-in-time score about their current security vulnerabilities, their risk and a score. It has an easy to use interface, reporting that is interpretable by both the technical and non-technical alike, and best of all - it's affordable for what you get!













