Help prevent 3rd party attacks with Detectify
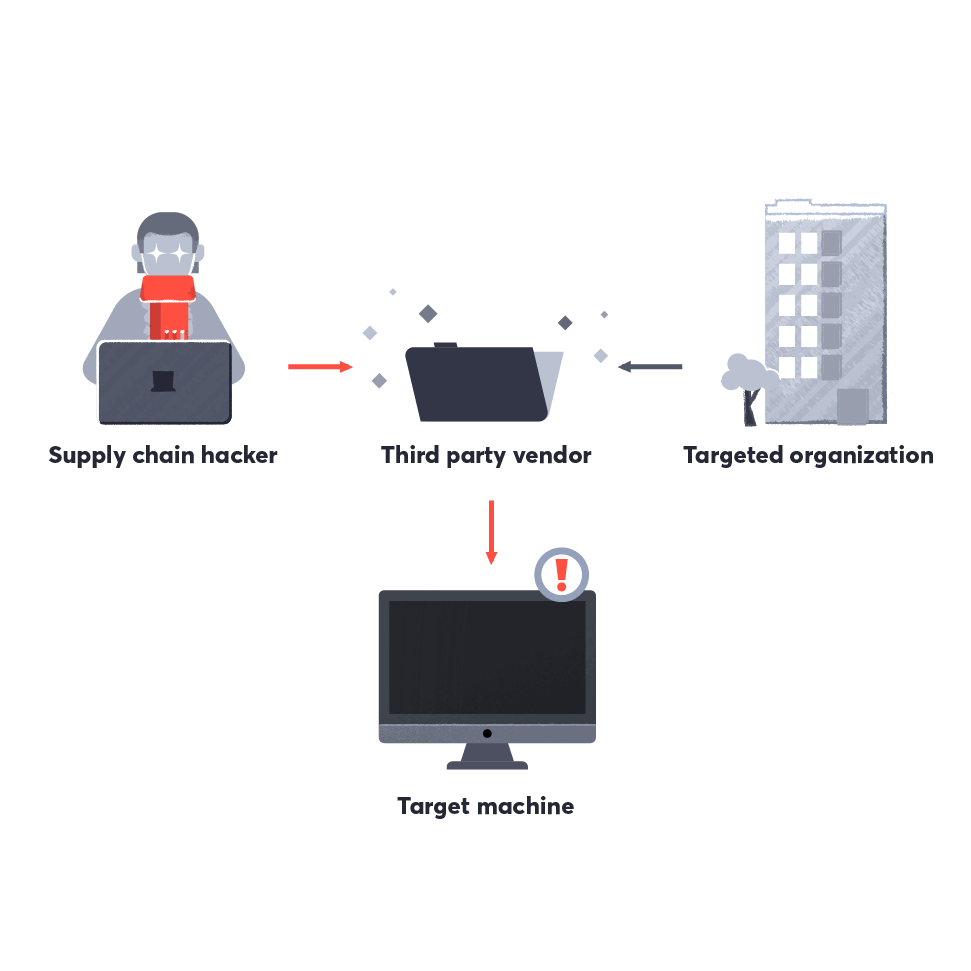
Your weakest links are often in the software you host
Hackers are looking for vulnerabilities that might seem insignificant but could be the target in larger, more sophisticated attacks. Our attack surface solution identifies vulnerabilities such as misconfigurations, XSS, SSRF, and RCE in products used in most technology stacks.
Running 1000s of tests to discover vulnerabilities
Publically available CVE often miss large portions of your attack surface. We're running daily scans across your entire attack surface to spot issues as they occur in production. We rely on payload-based tests to reduce the noise for your security teams.

Continuously, daily monitoring
We run more frequent scans compared to many other EASM solutions. Continuous monitoring of your attack surface means you will know as soon as an asset is affected.
Vulnerabilities sourced from the crowd
The latest security knowledge is automated from our global network of ethical hackers, Crowdsource, who detect commonly exploited vulnerabilities.

Ted M
President
Small Business

“Detectify is a powerful tool that every business should have”
Detectify provides my customers with a point-in-time score about their current security vulnerabilities, their risk and a score. It has an easy to use interface, reporting that is interpretable by both the technical and non-technical alike, and best of all - it's affordable for what you get!
Keep up with what hackers are doing
Discover, assess, prioritize and remediate your attack surface
Start 2-week free trialCurious to see what we'll find in your tech stack?
Start vulnerability testing to find exploitable anomalies across your attack surface to prevent 3rd party attacks.