Application security testing reimagined
Discover, classify, and scan all assets across your attack surface with DAST methods. Secure your domains, apps, and APIs. Go hack yourself!


How does Detectify work? Watch a short demo
AppSec teams use Detectify to expose how attackers will exploit their Internet-facing applications. See how you can do the same.
Discover our products
One solution for comprehensive coverage of your attack surface
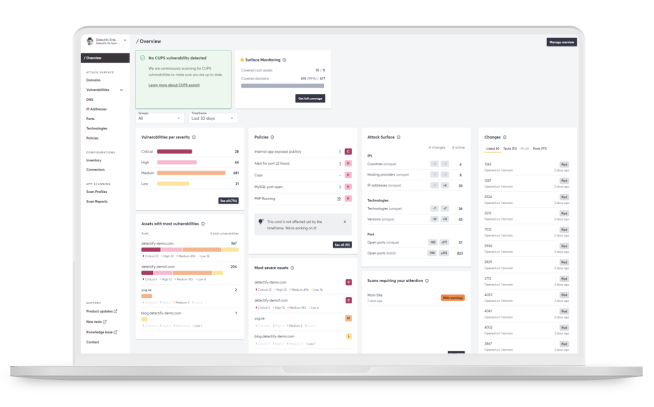
Surface Monitoring
Continuously discover and monitor all Internet-facing assets that you host with Surface Monitoring.
Cover your entire public DNS footprint, including ports
No complex configurations to get started
Fingerprint your tech stack
Application Scanning
Find and remediate business-critical vulnerabilities in custom-built apps with advanced crawling and fuzzing.
Render and crawl a custom-built application for in-depth findings
Maintain state and test authenticated areas
Scan massive applications with smart page filters
Broader and deeper coverage
A platform that provides evolving coverage across all your exposed assets
Surface Monitoring gives a comprehensive view of your attack surface, while Application Scanning provides deeper insights into custom-built applications. We recommend combining both products for the most comprehensive attack surface coverage.
Detectify is enterprise ready
For organizations with large amounts of domains and subdomains, we offer a flexible, scalable, and customized offering. Contact our sales team to learn more.
Enterprise add-ons include:
SSO / SAML
Extended authentication control with SSO and SAML.
Custom pricing
Custom pricing based on your attack surface and needs.
Dedicated CSM
Dedicated Customer Success Manager ready to partner with you.
Smooth onboarding
Save time with domain verification and let us set things up for you.
Multi-team Setup
Multi-team setup is available for flexible organizing of assets, access levels, and results.
Custom integrations
Tailor integrations specifically to your workflows, even outside of standard recipes.
Custom terms
Custom legal terms and security questionnaires.
Access to our API
Level up how you integrate Detectify with our versatile API.
Helping security teams cover their evolving attack surface

A solution that focuses on only producing relevant results
A solution that only produces relevant results
Before we even begin testing a single asset, we have already taken several steps to ensure the results are relevant and accurate. Leveraging 100% payload-based testing saves your team from spending precious time validating information.

An easy-to-use tool to immediately start scanning
An easy-to-use tool to immediately start scanning
Detectify doesn’t require hours of work to onboard and manage. Get started in no-time using cloud connectors and easily integrate results into your existing workflows. Get the most out of the platform with powerful integrations and API.
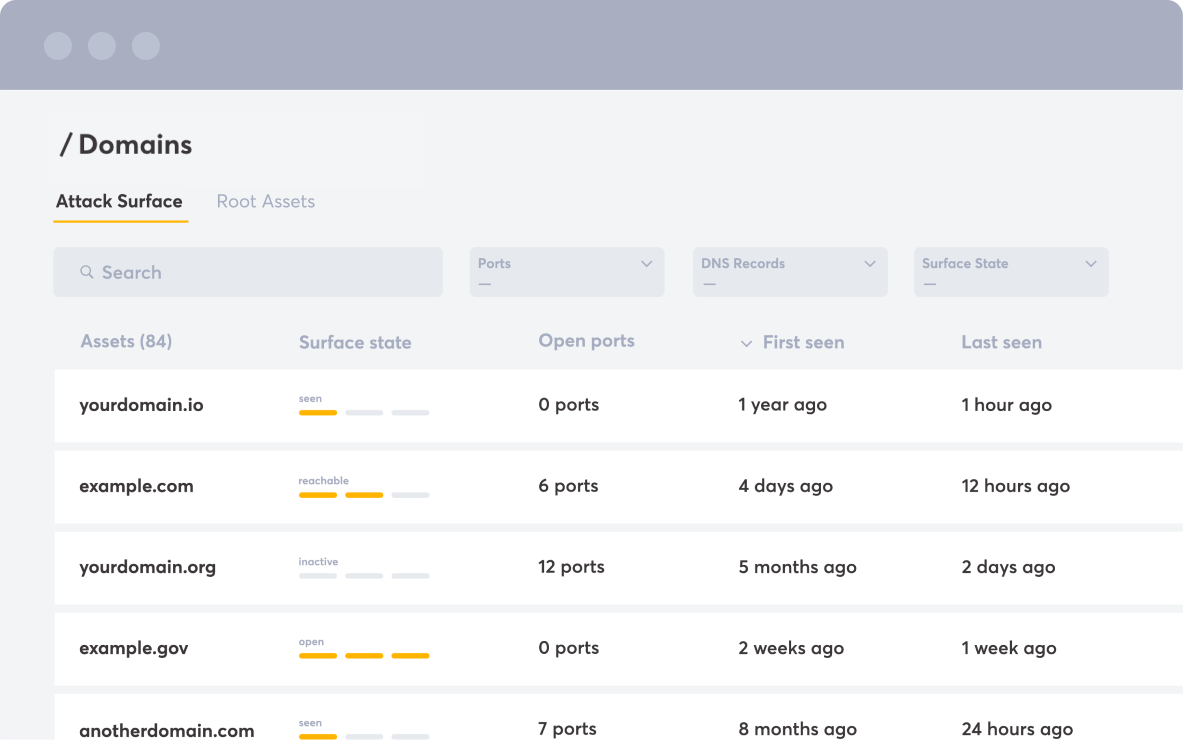
The only solution for dynamic testing on all your external assets
The only solution for dynamic testing on all your external assets
Detectify goes beyond merely identifying what's on the attack surface. Security teams rely on Detectify to scan every exposed asset using dynamic application testing methodologies, track attack surface changes, and receive guidance on effectively optimizing their resources.

Automated attacks fuelled by elite ethical hackers are built into our expert-built engines
Automated attacks fuelled by elite ethical hackers are built into our expert-built engines
From pioneering subdomain takeover tests to crowdsourcing vulnerability research, including hundreds of 0-days, we have always sought to automate human ingenuity. We build our engines so that we can move at speed and scale.
Industry use cases
Advanced application security testing for modern organizations

For technology organizations
Helping technology organizations manage digital transformation, secure digital products, and understand risks from M&A activities.

For consumer packaged goods organizations
Complete attack surface coverage for CPG organizations experiencing challenges in securing their digital products, and more.

For media & gaming organizations
Secure what you're hosting in the cloud and your multi-cloud architecture with Detectify.

Detectify crowdsource
The power of ethical hackers
Crowdsource, our community of ethical hackers, constantly discovers vulnerabilities across widely-used technologies. Detectify's repository of unique vulnerabilities is continuously growing thanks to Crowdsource - researchers have submitted over 1,765 modules, 300+ 0-days were received in 2020-21, and nearly 240,000 vulnerabilities have been found in customer assets.
ethical hackers
400+
0-days (2020/21)
300+
modules RECEIVED
1,765+
Testimonials
See what our customers think
Don't just take our word for it. We've helped several of the world's most popular digital product companies, organizations with many subsidiaries, and those with issues in third-party software and supply chains stay secure.
Read case studies
Marcin Hoppe
SENIOR ENGINEERING MANAGER
Auth0
“There are a lot of extremely noisy tools, and they generate a lot of findings, but to get to the true positives, you have to spend a lot of time analyzing the results. So we were very happy with the low rate of Detectify's false positives.”

Michelle Tolmay
DIRECTOR OF INFORMATION SECURITY
PHOTOBOX
“With Surface Monitoring, we found subdomains we didn’t know we had. Not only would we likely not have found these subdomains, but we also wouldn’t have known about them until someone did something really nasty on one of them and held us to ransom over it.”

Catalin Curelaru
SECURITY TRIAGE LEAD
Visma
“We used other tools before, but we chose Detectify because it helps us reduce false positives and gets much information from the availability perspective.”
Certification and awards














